IT security researchers warn of new attack technique using the clipboard
IT security researchers at Proofpoint have discovered a new attack method in which attackers use social engineering and the clipboard.
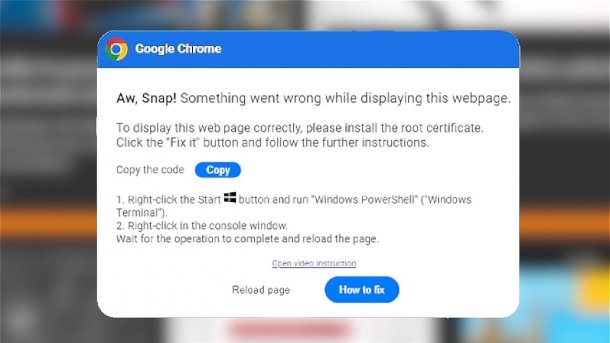
Supposed error message from the Chrome browser with various instructions.
(Image: Proofpoint/ Bearbeitung: heise online)
Security researchers from Proofpoint have identified an increasingly popular attack technique in which cyber criminals rely on social engineering. They use it to trick victims into executing malicious PowerShell code and installing malware.
The method was first used in early March 2024 by the initial access broker "TA571", which sells access to corporate networks. Since then, they have also been observed in ClearFake, Proofpoint reports. ClearFake is a malicious JavaScript framework that is used on compromised websites to spread further malware using drive-by-download technology. Victims receive an error message that pretends to come from a trusted source, such as the operating system. It suggests a problem and at the same time provides a solution in the form of a PowerShell command, which the victim only has to copy and execute.
Fake prompts
(Image: Proofpoint)
The first of these error messages was disguised as a Chrome web browser dialog. It contained instructions for the victim to click a button to copy a PowerShell script. It also included instructions to manually run the script as an administrator to fix the problem. If the instructions were followed, the user simply pasted the PowerShell script into the PowerShell command line window without any further action.
Videos by heise
If the victim follows the instructions, various malware programs such as Darkgate, Matanbuchus, NetSupport or Infostealer can be installed. Proofpoint classifies the danger as serious, as such threats are difficult to detect. In addition, antivirus software and endpoint detection and response programs have problems checking the contents of the clipboard. If companies notice suspicious activity, this should be reported to IT security immediately.
(mack)