Malvertising: Mac homebrew users targeted
Criminals have placed malicious ads on Google that redirect to a real-looking malware page instead of the homebrew website.
(Image: Screenshot / dmk)
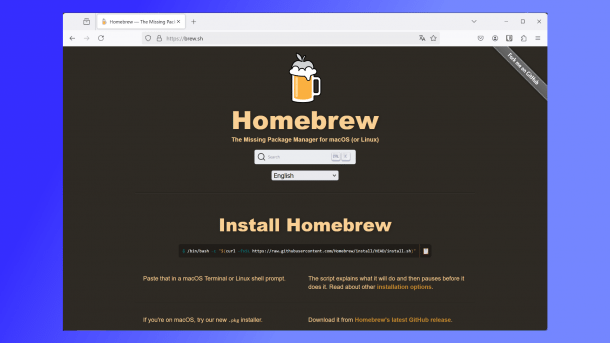
A malvertising campaign is running on Google: the perpetrators are trying to lure their victims with links that supposedly lead to the Homebrew website. If you look closely, you will discover the small error in the URL.
The brew.sh website is the official website for the Homebrew project, which makes various open source programs available for macOS. It is a – or, more correctly, the – open source package manager for Macs.
Website deceptively similar imitation
Homebrew is extremely popular. Therefore, victims could fall for such advertisements on Google, which supposedly refer to the Homebrew website. The advertisements also appear to use correct URLs: The URL "brew.sh" or "https://www.brew.sh" can be found in several places.
Videos by heise
If potential victims click on the link, they land on a website that looks confusingly similar to the original Homebrew website. However, the URL is "brewe[.].sh", with an additional "e" at the end. However, the console command given to install the brew system does not point to the regular homebrew installation script at "githubusercontent.com", but to a rather arbitrary, presumably compromised URL.
This was discovered by user Ryan Chenkie and reported on X. Meanwhile, smartscreen and URL filters of common web browsers hit the fraudulent malicious domain and warn against visiting the site. Moreover, if you ignore the warnings, the site is currently inaccessible.
Anyone who has installed Homebrew in the recent past should check whether the URL for the curl command pointed to trustworthy destinations or whether it appears to be arbitrary. The display of the bash history (.bash_history) can provide information about this. Calls to the curl command can be filtered out with the command cat ~/.bash_history | grep curl, for example.
The real Homebrew underwent an independent security audit in the middle of last year. This revealed 25 vulnerabilities, most of which have already been patched immediately.
(dmk)