AI tool clones websites and makes phishing child's play
A phishing toolkit automatically clones any website after entering the URL. Even laypersons can spy out passwords and access data in this way.
(Image: heise online / vbr)
Artificial intelligence is even finding its way into phishing software: the toolkit called "Darcula" enables laypersons to clone websites of well-known companies and use them for phishing scams, warns the IT security company Netcraft. New AI functions translate the fake pages into the language of the target country in a matter of seconds or create a deceptively real input mask from which address data or passwords are extracted.
Criminal users pay monthly for access to a range of different tools that enable data to be spied on. The developers' business model is therefore similar to the "Software as a Service" (SaaS) model.
No website is secure
In earlier versions, the software created fake pages from previously created templates. The scope of such attacks was therefore limited to popular services such as Google or Facebook, whose page layouts were stored in the templates. In the current version "Darcula v3", however, it is sufficient to enter the URL of the target page. The software then collects all assets such as images, fonts or colors and creates a copy that the user can edit. In theory, it is therefore possible to clone all publicly accessible websites. Attacks can therefore be much more targeted and aimed at specific target groups.
Empfohlener redaktioneller Inhalt
Mit Ihrer Zustimmung wird hier ein externes YouTube-Video (Google Ireland Limited) geladen.
Ich bin damit einverstanden, dass mir externe Inhalte angezeigt werden. Damit können personenbezogene Daten an Drittplattformen (Google Ireland Limited) übermittelt werden. Mehr dazu in unserer Datenschutzerklärung.
The embedded video shows how the software's AI functions simplify the process even further. With a request to the assistant, the software creates an input mask and designs it appropriately. Manual, often wooden-looking translations are no longer necessary. The AI translates the page into any language. Victims' mistrust of sites in foreign languages is potentially eliminated.
Videos by heise
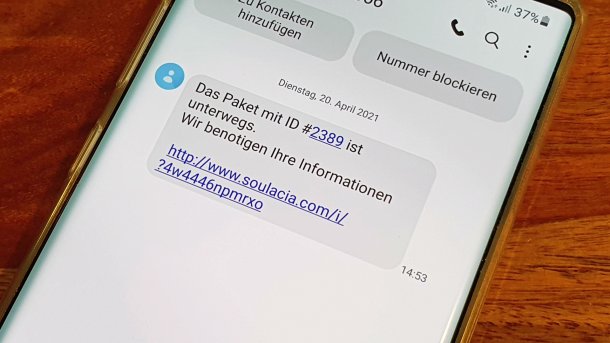
Victims are mainly found through "smishing", the mass sending of phishing messages. In these messages, the attackers pretend to be parcel services, banks or authorities, for example. In addition to traditional text messages, such attempts also take place via Rich Communication Services (RCS) or iMessage on Apple devices. In the case of text messages, phishing attempts can sometimes be intercepted by the spam filters of mobile phone providers. However, the end-to-end encryption of the RCS standard makes this impossible.
(acha)