Roundcube Webmail: More than 10,000 vulnerable instances in Germany
A code-smuggling gap in the Roundcube webmailer is already under attack. Tens of thousands of systems worldwide are still vulnerable.
(Image: Shadowserver)
The critical security vulnerability in Roundcube Webmail that became known last week is now being attacked on the Internet. The Shadowserver Foundation currently sees tens of thousands of vulnerable instances that are still freely accessible on the net. IT administrators should quickly download and install the available updates.
The Shadowserver Foundation provides information about thousands of vulnerable Roundcube systems on Mastodon. They are all susceptible to a vulnerability that allows authenticated users to inject and execute malicious code, as the “_from” parameter of a URL in “program/actions/settings/upload.php” is not checked, which leads to the deserialization of PHP objects (CVE-2025-49113 / EUVD-2025-16605, CVSS 9.9, risk “critical”). The vulnerability is being abused by criminals on the Internet, which is why the US IT security authority CISA added it to the Known Exploited Vulnerabilities Catalog (KEV) at the beginning of the week.
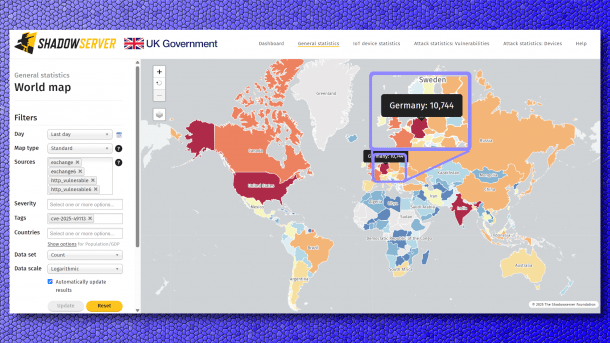
Roundcube: Tens of thousands of vulnerable systems open on the network
On Wednesday, the Shadowserver Foundation identified a total of 66,801 Roundcube webmail instances worldwide that are vulnerable. Of these, more than 15,000 systems are located in the USA, 12,000 in India and Germany is in third place with more than 10,500 vulnerable systems. Overall, the total number fell by around 18,000 systems; on Tuesday of this week, there were still just under 85,000 systems with the vulnerability in the network worldwide.
Videos by heise
Some admins are therefore doing their job and are already patching the vulnerable systems. IT managers should now urgently update to the no longer vulnerable versions Roundcube 1.5.10 and 1.6.11 or newer and thus secure their network environment against attacks. Unfortunately, neither CISA nor Roundcube provide any Indicators of Compromise (IOCs) that admins can use to check whether their systems have already been (successfully) attacked.
(dmk)