Wireshark 4.6: New functions for encrypted data
Version 4.6 of the free network analysis tool Wireshark brings improvements in decryption and export.
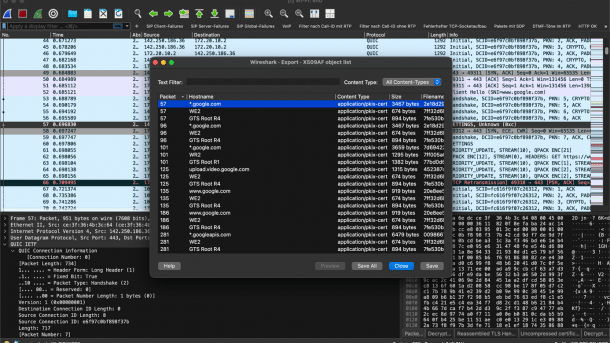
Wireshark 4.6 brings new export options for X.509 certificates extracted from the TLS handshakes of website requests.
- Benjamin Pfister
A key highlight of Wireshark 4.6.0, which has now been released, is the extended support for decrypting network protocols. Users can now decrypt MACsec-protected packets either based on the Secure Association Key (SAK) decrypted from the MKA dissector or the Pre-Shared Keys (PSK) configured in the MACsec dissector. In addition, the new version now enables the decryption of NTS-encrypted NTP packets (Network Time Security).
Another long-awaited feature is the export of X.509 certificates directly from Wireshark and the command-line tool Tshark. Security analysts and administrators can now quickly extract certificates from network traffic and use them to troubleshoot TLS connections. This is complemented by the new option of copying packet details and protocol information as HTML code, which is interesting for documentation purposes.
Good news for macOS users
There is also good news for macOS users: the standardized macOS installer avoids confusion by replacing the previous separate packages for ARM and Intel.
Videos by heise
Under the bonnet, there has been some version maintenance, such as Qt for the GUI to 6.9.3 and the Npcap driver for recording to v1.83 under Windows. The old WinPcap driver for recording is no longer supported. Wireshark 4.6.0 is now available for download for Windows, macOS, and Linux. Further details can be found in the release notes on the project website.
()