38C3: Framework "Phuzz" helps to detect errors in PHP web applications
Phuzz" is designed to detect security vulnerabilities in PHP web applications more effectively than other tools.
(Image: CCC/38C8)
PHP is still the dominant programming language on the web; a good three quarters of all websites are based on the scripting language because they use PHP-based content management systems such as WordPress, Drupal or Joomla. Security vulnerabilities in plug-ins and themes can give attackers access to sensitive data. Sebastian Neef, PhD student at the Chair of Security in Telecommunications at TU Berlin, presented "Phuzz" at the 38th Chaos Communication Congress (38C3) –, a coverage-guided fuzzing framework specifically designed for PHP web applications. It is designed to help both developers and security researchers to quickly find and fix vulnerabilities.
Security researchers use "fuzzing" as a technique to uncover vulnerabilities at an early stage: programs are automatically tested with numerous random inputs to detect unexpected behavior and thus potential security risks. Well-known examples include OSS-Fuzz, developed by Google for testing open source software, as well as American Fuzzy Lop (AFL) and its offshoot AFL++. In contrast to these tools, which mainly focus on binary applications, Phuzz is designed specifically for the requirements of modern web applications.
(Image: Sebastian Neef)
"Coverage-guided" approach optimizes fuzzing process
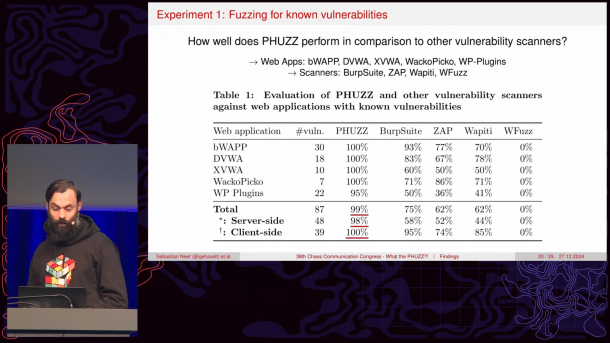
According to Neef, the special feature of Phuzz is the so-called "coverage-guided" approach: the framework analyzes which code areas are reached by the test inputs and adapts the further tests accordingly. Compared to other tools such as webFuzz, CeFuzz, Witcher or Atropos, the source code of the tested application does not have to be changed for this, according to the developer.
Phuzz is designed to detect seven different types of security vulnerabilities: SQL Injection, Command Injection, External Entity Injection, Path Traversal, Insecure Deserialization, Cross-Site Scripting and Open Redirection. The framework uses the open source extensions UOPZ, pcov and Xdebug for instrumentation. By supporting parallel fuzzing with multiple instances, Phuzz finds more server-side vulnerabilities than conventional "black box fuzzers", said Neef.
Videos by heise
More successful with PHP than "black box fuzzers"
By testing 183 popular WordPress plugins with over 300,000 active installations, Phuzz identified 1,019 API endpoints and discovered several previously unknown vulnerabilities, including two confirmed zero-day vulnerabilities in the Popup Builder plugin (CSRF Vulnerability) and another plugin (Local File Inclusion).
Currently, Phuzz can only handle multi-level and stateful actions to a limited extent and cannot hook into PHP expressions (such as eval, include, ...) with UOPZ. The performance can also be optimized in comparison to binary fuzzing. Neef provides the Phuzz framework as dockerized, modular open-source software on GitHub and invites users to participate.
More details on how it works can be found in the research paper published under Open Access and the recording of the 38C3 presentation.
(vza)